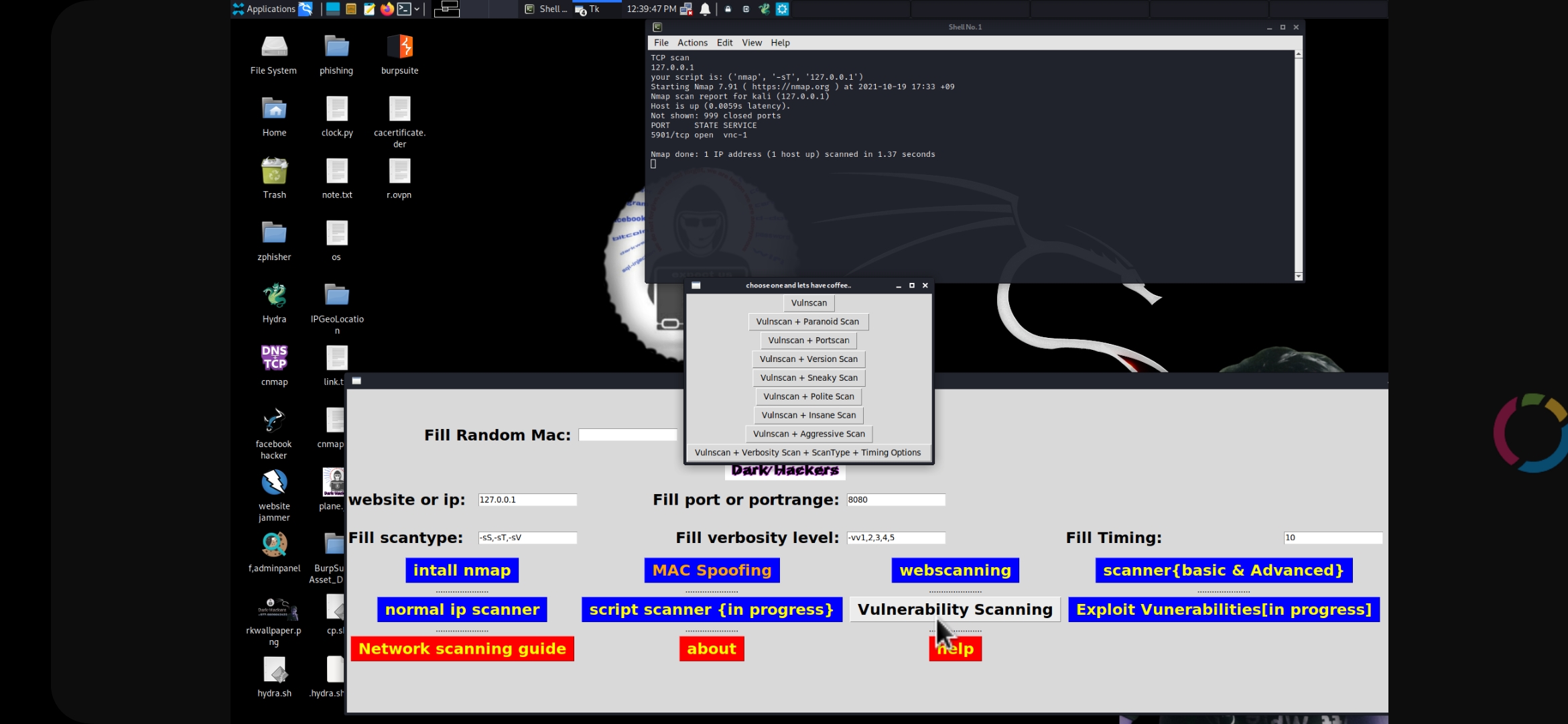
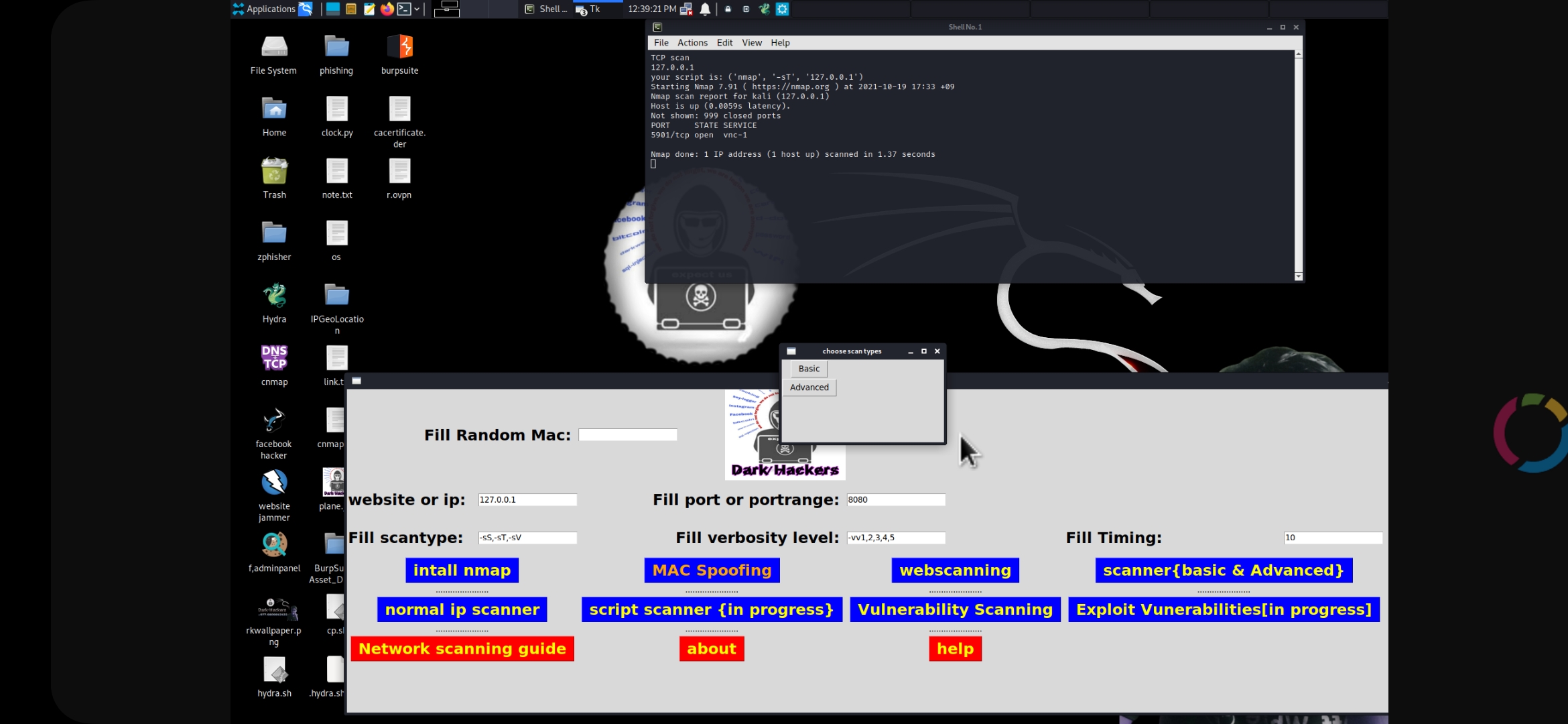
CNMAP-GUI-
OpenPort scanner GUI tool (CNMAP) as you know it is the advanced tool to find open port, firewalls and we also added here heartbleed scanning, mac spoofing, tcp scanning, udp scanning and so more. we hope you will do your things fastly by helping of this tool. best of
#to use this tool on android, do the following on termux.
*. apt update
*. apt upgrade
*. apt install wget
*. chmod +x install-nethunter-termux
*. ./install-nethunter-termux
(After that wait sometimes and if it ask for any kind of permision then give it.)
After completing setting up
Type....
*. nh kex (first time it must be ask for set password, just set a new password )
Note: if "nh kex" show "no matching vncserver" and doesnot start, Then simply search the solution on youtube.
Now download vncserver Open it Start Set address (127.0.0.1:5901) (sometimes 5901 must be 5902) And fill any name and start
And boom your desktop created|
Now open terminal there
And clone our tool by
*. git clone https://github.com/nepalese-noob/CNMAP-GUI-
*. cd CNMAP-GUI-
*. sudo apt-get install python3-tk (password: kali)
*. sudo easy_install pip
*. sudo pip install pillow
*. python3 cnmap.py
And boom!
Best wishes :
Hawkhacker
Twinkle sharma
Mr. Aayus
Aur Me khud